Unlike an event that takes out the power for a few hours or days, Ransomware has the potential for a greater and far deeper reaching impact on the productivity and operations of running a business.
Early in the summer at one of the customer events with our partner Covenco, I spent time with Paul Szelesi, Senior EMEA Solution Architecture Director at Veeam. These events provide first hand insight into the issues facing our partners and their customers, but it also highlights the reality of threats facing people and their businesses. Paul provided a fantastic presentation on Veeam’s capabilities and how they are complemented with Zadara’s own capabilities, but the core message is that organisations must assume a data breach will happen and provide separation between systems to protect against the threats of complex Ransomware attacks.
As we’ve highlighted in this blog series, Ransomware attacks are becoming more and more sophisticated, attacking the very infrastructure that is looking to protect us. Therefore patching and keeping systems up to date is a critical part of our daily systems security posture. As reported recently in SC Magazine, our backup and recovery systems are increasingly under attack; a recent Veeam vulnerability with a patch available is being exploited by attackers in organisations that have failed to patch their systems. This confirms the well documented trend recently highlighted in the Veeam Ransomware Trends Report 2023.
In our latest webinar with Steve Firmes, Senior Solutions Architect Product Management-Alliances at Veeam, we pushed out a deeper message around Defence in Depth and why it is important to have a multilayer approach. You must assume you have been breached and design your infrastructure in a security first posture.
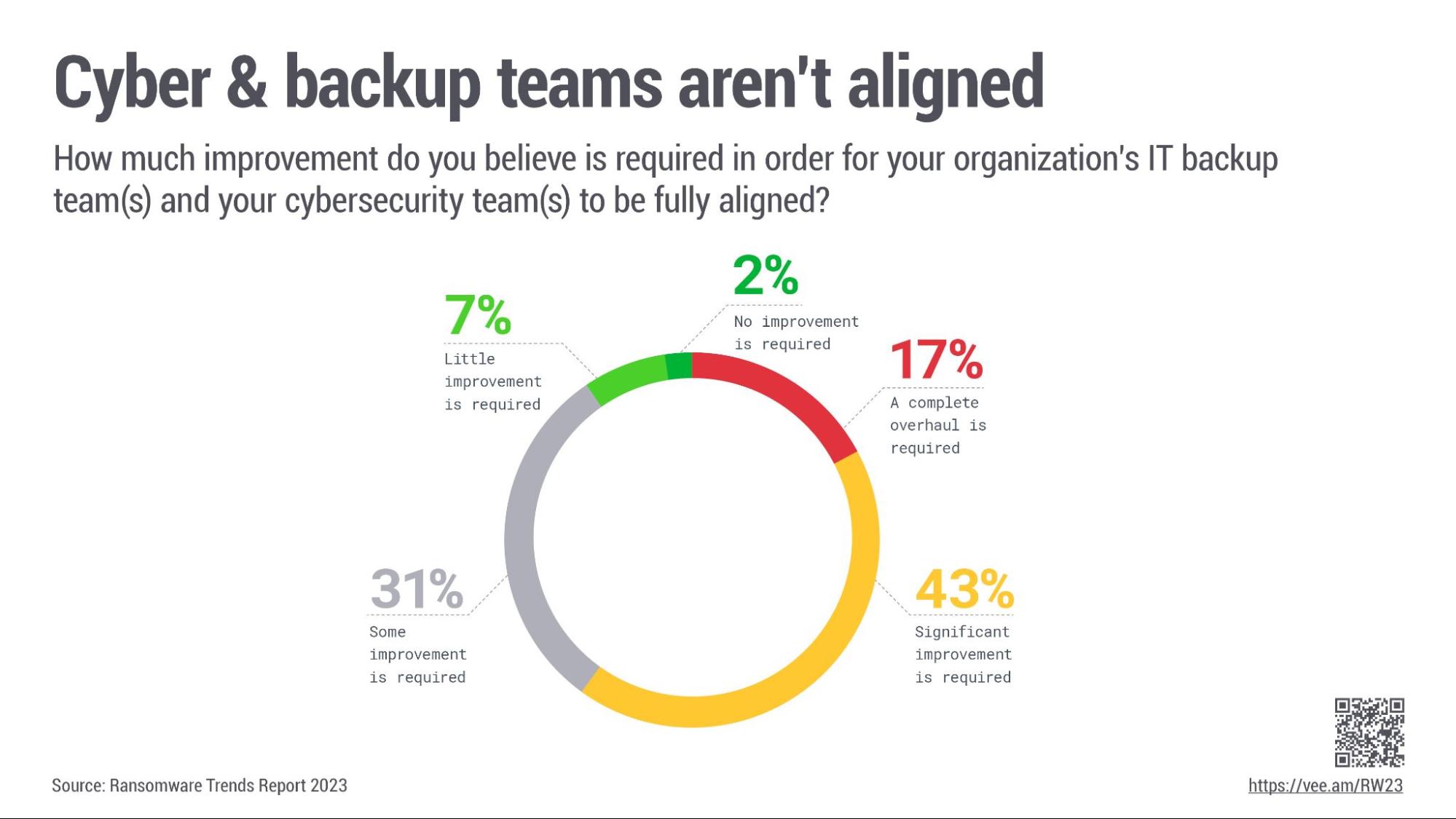
The UK National Cyber Security Centre has some great guidance on beginning this deeper look into your architecture with its secure design principles. This means aligning your teams to have a secure stance. Veeam’s Ransomware trends 2023 captures this well.
Design for Defence in Depth
First you need to understand your environments, all aspects of what they do and why, find your blind spots and mitigate them before your attackers do. You need to be monitoring your systems and you need to be monitoring into a secure environment. You want to make sure the logs you are gathering are not able to be compromised too. A ransomware attack is a crime scene, so you should think of your logs as evidence. With this in mind you need to preserve all evidence, not just your log data, it may also mean that your primary infrastructure becomes unusable until the forensic analysis is complete.
VeeamOne can monitor and provide comprehensive reporting and alerting against backup and infrastructure changes. When combined with Zadara’s Virtual Private Storage Arrays (VPSA) capabilities you can provide an isolated repository to underpin the VeeamOne database – ensuring that any attack vector is minimised.
Now if you forward the alerts via syslog to a one way repository you can further enhance your posture. The alerting may be part of a more comprehensive environment, such as a Crowdstrike LogScale, Splunk or utilising a Grafana Loki environment as described by Jorge de la Cruz in his blog.
You cannot defend what you cannot see and observe, but you also need to protect the observability tools, in line with good design principles making a compromise difficult to spread but easier to see has to be a good thing.
The Zadara Difference
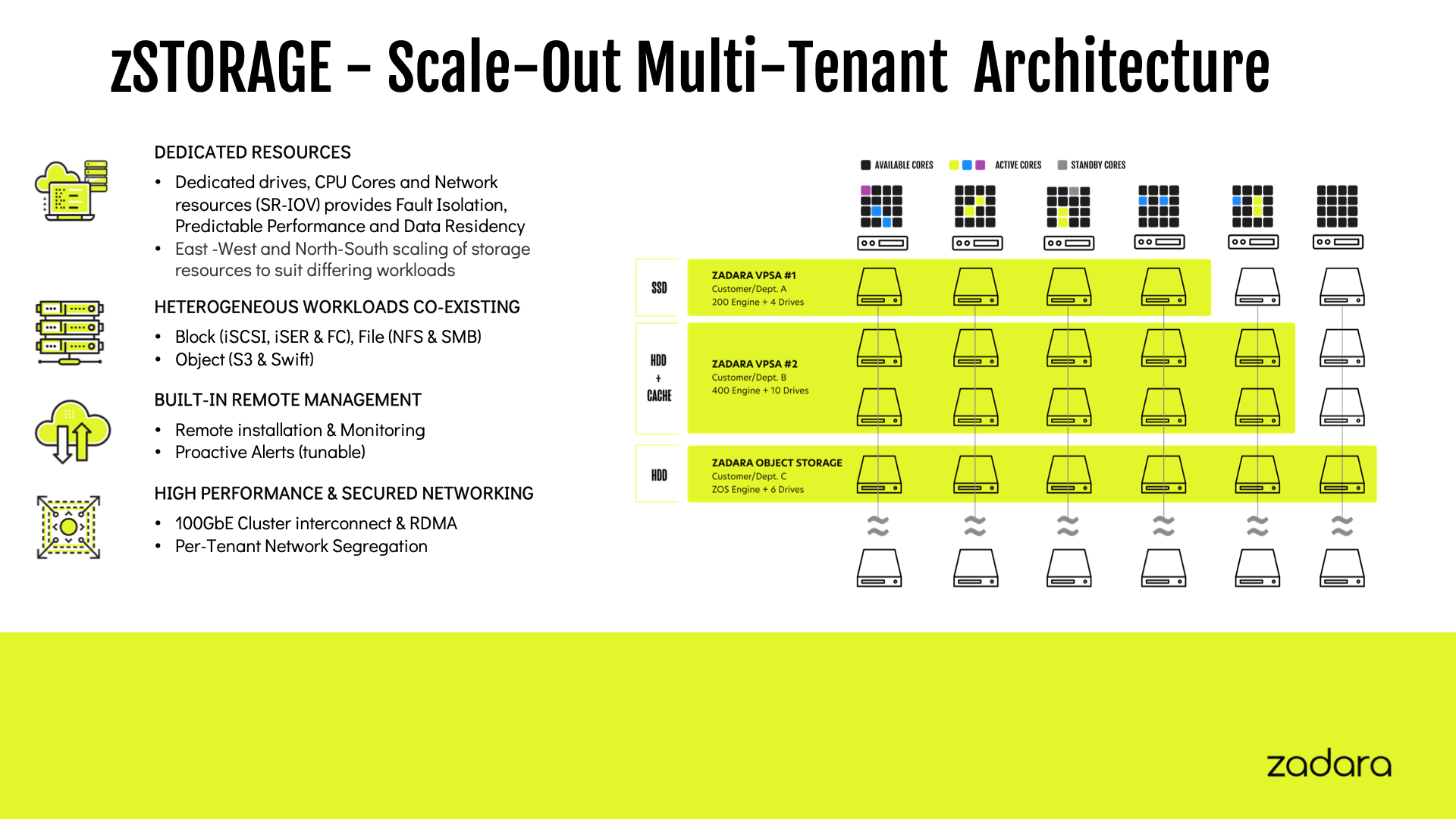
This is where Zadara sets itself apart, unlike an Object Storage only vendor or Hyperscale Cloud vendor, Zadara has the ability to provide multiple levels of storage to support all aspects of a business’s storage needs across all protocols, Block, File and Object. Zadara’s storage is further complemented by our cloud compute capabilities to provide an infrastructure that can scale dynamically, from small to medium to large, to provide comprehensive recovery solutions, whatever your environment.
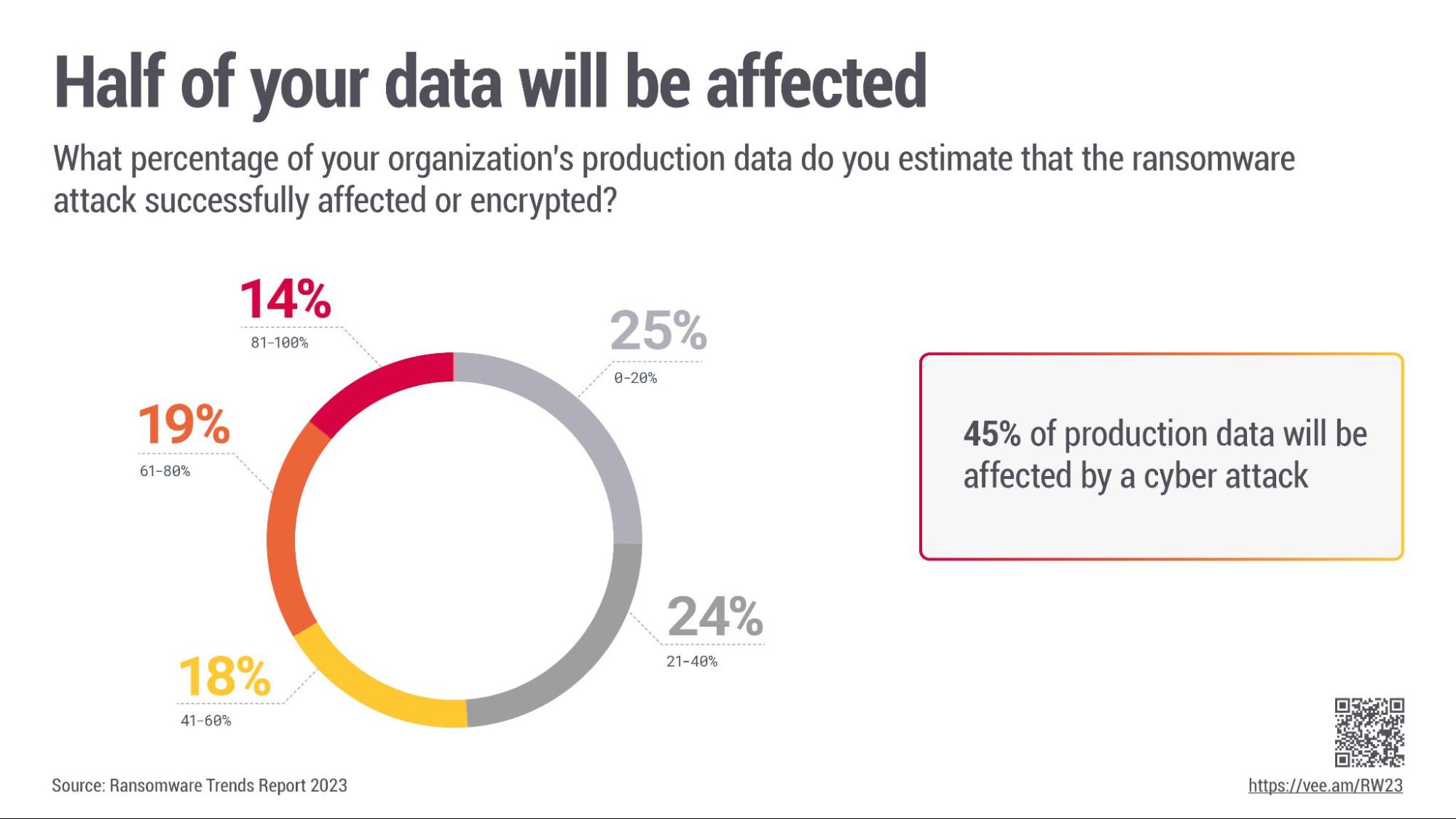
With Zadara as your storage infrastructure partner, you can create multiple levels and separation of systems in a way that you do not need to with competing solutions. Should one VPSA’s data be compromised, you are more in control and able to limit the impacts. Using Multi-Factor Authentication with each VPSA makes it harder to go east-west through your environment with Zadara. When you assume breach, you must ensure any compromise is limited in impact, as outlined in the Veeam 2023 Ransomware report. The combination of adding Zadara into your Veeam designs enables a more robust security defence in depth strategy.
The Zadara patented architecture ensures dedicated resources so that you don’t have noisy neighbour impacts when your database and backup applications are running concurrently on the same platform, or your Object Storage needs change over time, or you need to move drives from being NAS to Object Storage. This dynamic flexibility with segregation is unmatched in the industry.
When you are looking at your technology stack, identifying all of the attack points, how are you going to mitigate them, please remember with Zadara, there are options that can help you to accomplish your goals with choice and flexibility. Whether that be different media (HDD and SSD), different access protocols, different management layers, encryption on or off per volume, dedupe and compression on or off per volume, immutable Object Storage, KMIP integration and many more.
Reach out to us and let us see how we can help you to provide defence in depth.